Helpful Links
Published:
A list of all the posts and pages found on the site. For you robots out there is an XML version available for digesting as well.
Published:
Page not found. Your pixels are in another canvas.
Bachelor of Digital Science, Universiti Brunei Darussalam, Digital Science, 2023
This is a page not in th emain menu
Published:

Published:

Published:

Published:

Published:

Published:

Published:

Published:
Published:

Published:

Published:

Published:

Published:

Published:

Published:

Published:

Published:

Published:

Published:

Published:

Published:

Published:

Published:

Published:

Published:

Published:

Published:

Published:

Published:

Published:

Published:

Published:

Published:

Published:

Published:

Published:
This post covers Data Analysis using R.
Published:
Published:
Published:
Published:

Published:

Published:
This lesson covers an introduction to Jupyter Notebook/Lab.
Published:
This post covers image classification, nearest neighbor classifier, k-nearest neighbor classifier and validation sets from cs231n.
Published:
This lesson covers CNN for CIFAR10
Published:
This lesson covers PyTorch Tutorial, https://pytorch.org/tutorials/beginner/basics/intro.html
Published:
This lesson covers PyTorch Tutorial, https://pytorch.org/tutorials/beginner/basics/intro.html
Published:
This lesson covers PyTorch Tutorial, https://pytorch.org/tutorials/beginner/basics/intro.html
Published:
This lesson covers PyTorch Tutorial, https://pytorch.org/tutorials/beginner/basics/intro.html
Published:
This lesson covers PyTorch Tutorial, https://pytorch.org/tutorials/beginner/basics/intro.html
Published:
This lesson covers PyTorch Tutorial, https://pytorch.org/tutorials/beginner/basics/intro.html
Published:
This lesson covers PyTorch Tutorial, https://pytorch.org/tutorials/beginner/basics/intro.html
Published:
This lesson covers PyTorch Tutorial, https://pytorch.org/tutorials/beginner/basics/intro.html
Published:
This lesson covers PyTorch Tutorial, https://pytorch.org/tutorials/beginner/basics/intro.html
Published:
Chapter 6
Published:

Published:
This page covers the discovery year process and opportunities.
Published:
This post covers detecting outliers.
Published:
This post covers Multivariate Visualization.
Published:
This post covers Bivariate Visualization.
Published:
This post covers Univariate Data Visualization.
Published:
This post covers Data Assessing and Cleaning.
Published:
This post covers Data Gathering.
Published:
This post covers Data Wrangling.
Published:
This post covers Introduction to Pandas.
Published:
This post covers Introduction to Python Programming.
Published:
Download Python.
Published:
This page covers projects completed by Students.
Published:
This lesson is from Adversarial Robustness - Theory and Practice
Published:
This lesson is for help.
Published:
This lesson covers Linear Regression.
Published:
Published:
Published:
This post covers MNIST implementation of ICLR 2015 paper “Explaining and Harnessing Adversarial Examples”
Published:
This post explains Chi-square Test.
Published:
This post provides t Table.
Published:
This post covers Hypothesis Testing.
Published:
This post covers Estimation.
Published:
This post explains creating slides using Jupyter Notebook.
Published:
This post covers Sampling Distributions Example.
Published:
This post covers Probability Distributions.
Published:
This post covers Normal Distribution from https://www.mathsisfun.com/data/standard-normal-distribution.html and https://www.mathsisfun.com/data/standard-deviation.html
Published:
This post provides Z Table.
Published:
This post covers Sampling Distributions.
Published:
This lesson is on Machine Learning notes.
Published:
This post covers introduction to Image Classification using Deep Learning.
Published:
This post covers introduction to Image Classification using Deep Learning.
Published:
This post covers CNN Architecture from cs231n.
Published:
This post covers CNN Architecture from cs231n.
Published:
This post covers Optimization and Backpropogation from cs231n.
Published:
This post covers Optimization and Gradient Descent from cs231n.
Published:
This post covers Introduction to some other python libraries.
Published:
This post covers introduction to Neural Network using MNIST dataset.
Published:
This post covers introduction to Convolution Neural Network using MNIST dataset.
Published:
This post covers certain formulas useful for Deep Learning.
U.S. Patent Publication, 2015
The patent describes a safe card that that by default is in a blocked state so that no transcation can be made. The safe card can be activated for a limited time by an authorized user for the transaction.
Recommended citation: Aneja, N., and Aneja, S. "Anti-fraud computer implemented method for financial card transaction." U.S. Patent Publication 2015/0339,657, filed May 23, 2014, published Nov 26, 2015. https://patentimages.storage.googleapis.com/06/22/8e/674c30a57d0fe8/US20150339657A1.pdf
U.S. Issued Patent, 2019
The patent describes a method to create a social network based on dynamic interests of users and using ad-hoc networking. A user of mobile device can identify another user who is close by and has similar interests. Dynamic interests of the users can be extracted or identified based on mobile usage, browsing history, places traveled, and other user actions. Users are notified if another user who is similar more than a threshold is present nearby. The system also facilitates communication between users by way of chatting, file sharing, image sharing etc.
Recommended citation: Aneja, N., and Gambhir, S. "Method and system for Ad-hoc Social Networking and Profile Matching." U.S. Patent 10,264,609, filed Dec 28, 2015, issued April 16, 2019. https://patentimages.storage.googleapis.com/0f/63/b5/a0d9ef4311bf34/US10264609B2.pdf
U.S. Issued Patent, 2020
The discloosure presents unified instant messaging application/service that enables to concurrently send messages via online mode using internet and Offline or Airplane mode
Recommended citation: Aneja, S., Aneja. N., and Petra, I. "Instant messaging for mobile device with offline and online mode." U.S. Patent 10,834,035, filed Dec 28, 2015, issued Nov 10, 2020. https://patentimages.storage.googleapis.com/58/d4/f7/58ebe5626a9362/US10834035.pdf
Published:
Detecting Fake News using language features 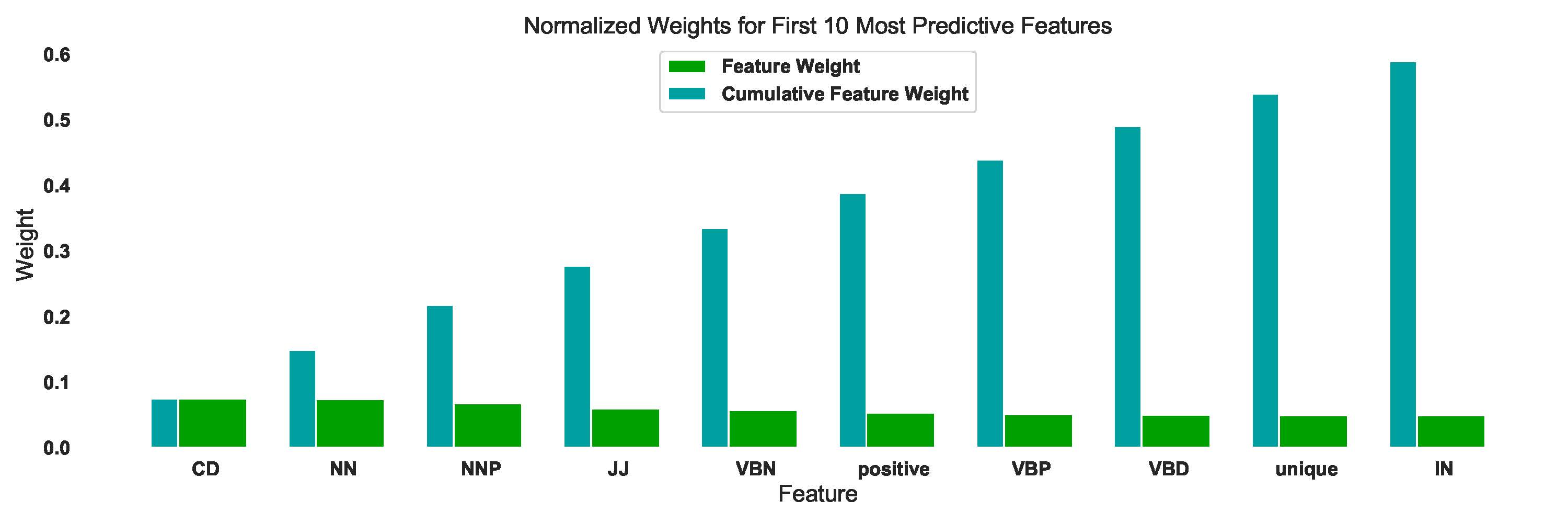
Published:
Implementation of convolutional neural network to clone driving behavior using Keras. The model outputs a steering angle to an autonomous vehicle.
Published:
Transfer Learning for detecting cancer from Histopathology images 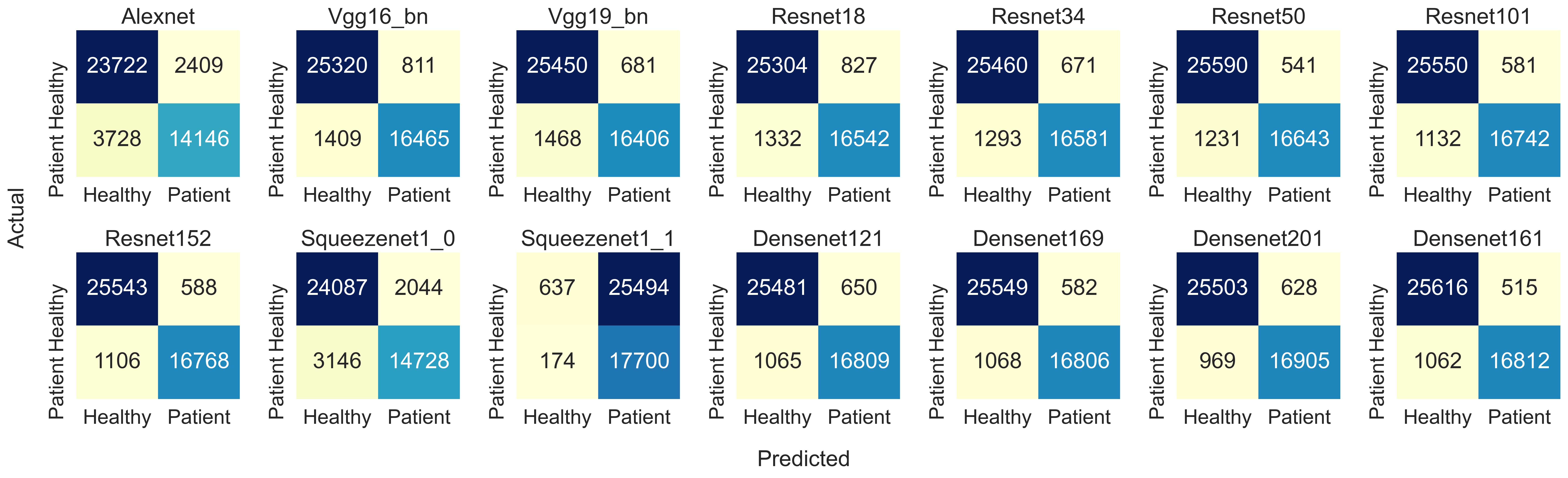
Published:
NL-Augmenter 🦎 → 🐍 A Framework for Task-Sensitive Natural Language Augmentation
Published in International Conference on Networking, International Conference on Systems and International Conference on Mobile Communications and Learning Technologies (ICNICONSMCL'06), 2006
(Conference Publication)
Recommended citation: Sandhya Khurana, Neelima Gupta, Nagender Aneja "Reliable ad-hoc on-demand distance vector routing protocol." International Conference on Networking, International Conference on Systems and International Conference on Mobile Communications and Learning Technologies (ICNICONSMCL'06), 2006. pp. 98--98 doi: 10.1109/ICNICONSMCL.2006.183 https://ieeexplore.ieee.org/document/1628344
Published in Sixth International Conference on Networking (ICN'07), 2007
(Conference Publication)
Recommended citation: Sandhya Khurana, Neelima Gupta, Nagender Aneja "Minimum exposed path to the attack (MEPA) in mobile ad hoc network (MANET)." Sixth International Conference on Networking (ICN'07), 2007. pp. 16--16 doi: 10.1109/ICN.2007.57 https://ieeexplore.ieee.org/document/4196209
Published in National Conference on Recent trends in computer science and Information Technology (RTCSIT), 2012
(Conference Publication)
Recommended citation: Nagender Aneja, Sapna Gambhir "Various Issues in Ad-hoc Social Networks (ASN)." National Conference on Recent trends in computer science and Information Technology (RTCSIT), 2012. https://naneja.github.io/files/pubs/Various-Issues-in-Ad-hoc-Social-Networks.pdf
Published in International Journal of Scientific and Engineering Research, 2013
(Journal Publication)
Recommended citation: Sapna Gambhir, Nagender Aneja "Ad-hoc social network: A comprehensive survey." International Journal of Scientific and Engineering Research, 2013. vol. 4 pp. 156--160 https://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.415.7643&rep=rep1&type=pdf
Published in Research Journal of Applied Sciences, Engineering and Technology, 2014
(Journal Publication)
Recommended citation: Nagender Aneja, Thomas George "Verification of Forecasts from High Resolution Numerical Weather Prediction Model." Research Journal of Applied Sciences, Engineering and Technology, 2014. vol. 8 pp. 1255--1258 doi: 10.19026/rjaset.8.1092 https://maxwellsci.com/jp/mspabstract.php?jid=RJASET&doi=rjaset.8.1092
Published in Social Networking, 2014
(Journal Publication)
Recommended citation: Nagender Aneja, Sapna Gambhir "Geo-social profile matching algorithm for dynamic interests in ad-hoc social network." Social Networking, 2014. vol. 3 pp. 240 doi: 10.4236/sn.2014.35029 https://www.scirp.org/journal/paperinformation.aspx?paperid=51108
Published in 2015 IEEE International Conference on Computational Intelligence & Communication Technology, 2015
(Conference Publication)
Recommended citation: Nagender Aneja, Sapna Gambhir "Geo-social semantic profile matching algorithm for dynamic interests in ad-hoc social network." 2015 IEEE International Conference on Computational Intelligence & Communication Technology, 2015. pp. 354--358 doi: 10.1109/CICT.2015.50 https://ieeexplore.ieee.org/document/7078725
Published in 2015 International Conference on Soft Computing Techniques and Implementations (ICSCTI), 2015
(Conference Publication)
Recommended citation: Sapna Gambhir, Nagender Aneja, Samridhi Mangla "Need of ad-hoc social network based on users' dynamic interests." 2015 International Conference on Soft Computing Techniques and Implementations (ICSCTI), 2015. pp. 52--56 doi: 10.1109/ICSCTI.2015.7489562 https://ieeexplore.ieee.org/document/7489562
Published in 2016 3rd International Conference on Computing for Sustainable Global Development (INDIACom), 2016
(Conference Publication)
Recommended citation: Sapna Gambhir, Samridhi Mangla, Nagender Aneja "Software Design for social profile matching algorithm to create ad-hoc social network on top of android." 2016 3rd International Conference on Computing for Sustainable Global Development (INDIACom), 2016. pp. 3450--3454 https://ieeexplore.ieee.org/document/7724906
Published in Research Journal of Applied Sciences, Engineering and Technology, 2016
(Journal Publication)
Recommended citation: Nagender Aneja, Sapna Gambhir "Middleware architecture for ad-hoc social network." Research Journal of Applied Sciences, Engineering and Technology, 2016. vol. 13 pp. 690--695 doi: 10.19026/rjaset.13.3342 https://maxwellsci.com/msproof.php?doi=rjaset.13.3342
Published in NoSQL: Database for Storage and Retrieval of Data in Cloud, 2017
(Book Chapter)
Recommended citation: Sandhya Aneja, Nagender Aneja "Security and Privacy: Challenges and Defending Solutions for NoSQL Data Stores." NoSQL: Database for Storage and Retrieval of Data in Cloud, 2017. pp. 237--250 doi: 10.1201/9781315155579-13 https://www.taylorfrancis.com/chapters/edit/10.1201/9781315155579-13/security-privacy-challenges-defending-solutions-nosql-data-stores-sandhya-aneja-nagender-aneja
Published in IEEE Internet Technology Policy Community; White Paper, 2017
(IEEE White Paper)
Recommended citation: G Corser, G Fink, J Bielby "Internet of Things (IoT) Security Best Practices." IEEE Internet Technology Policy Community; White Paper, 2017. https://standards.ieee.org/wp-content/uploads/import/documents/other/whitepaper-internet-of-things-2017-dh-v1.pdf
Published in IEEE Internet Technology Policy Community White Paper, 2017
(IEEE White Paper)
Recommended citation: Mohammed Aledhari, Sukanya Mandal, Nagender Aneja, Mikael Dautrey, Rajesh Nighot, Prasad Mantri, Jared Bielby "Protecting Internet Traffic: Security Challenges and Solutions." IEEE Internet Technology Policy Community White Paper, 2017. https://standards.ieee.org/wp-content/uploads/import/documents/other/whitepaper-protecting-internet-traffic-dh-v1.pdf
Published in Wireless Personal Communications, 2017
(Journal Publication)
Recommended citation: Sapna Gambhir, Nagender Aneja, Liyanage De "Piecewise maximal similarity for ad-hoc social networks." Wireless Personal Communications, 2017. vol. 97 pp. 3519--3529 doi: 10.1007/s11277-017-4683-4 https://link.springer.com/article/10.1007/s11277-017-4683-4
Published in Wireless Personal Communications, 2017
(Journal Publication)
Recommended citation: Nagender Aneja, Sapna Gambhir "Social profile aware AODV Protocol for ad-hoc social networks." Wireless Personal Communications, 2017. vol. 97 pp. 4161--4182 doi: 10.1007/s11277-017-4718-x https://link.springer.com/article/10.1007/s11277-017-4718-x
Published in Mobile Information Systems, 2018
(Journal Publication)
Recommended citation: Nagender Aneja, Sapna Gambhir "Profile-based ad hoc social networking using Wi-Fi direct on the top of android." Mobile Information Systems, 2018. vol. 2018 doi: 10.1155/2018/9469536 https://www.hindawi.com/journals/misy/2018/9469536/
Published in 2018 IEEE international conference on internet of things and intelligence system (IOTAIS), 2018
(Conference Publication)
Recommended citation: Sandhya Aneja, Nagender Aneja, Md Islam "IoT device fingerprint using deep learning." 2018 IEEE international conference on internet of things and intelligence system (IOTAIS), 2018. pp. 174--179 doi: 10.1109/IOTAIS.2018.8600824 https://ieeexplore.ieee.org/abstract/document/8600824
Published in International Conference on Deep Learning, Artificial Intelligence and Robotics, 2019
(Conference Publication)
Recommended citation: Nagender Aneja, Sandhya Aneja "Detecting Fake News with Machine Learning." International Conference on Deep Learning, Artificial Intelligence and Robotics, 2019. pp. 53--64 doi: 10.1007/978-3-030-67187-7_7 https://link.springer.com/chapter/10.1007/978-3-030-67187-7_7
Published in 2019 1st International Conference on Advances in Information Technology (ICAIT), 2019
(Conference Publication)
Recommended citation: Nagender Aneja, Sandhya Aneja "Transfer learning using CNN for handwritten Devanagari character recognition." 2019 1st International Conference on Advances in Information Technology (ICAIT), 2019. pp. 293--296 doi: 10.1109/ICAIT47043.2019.8987286 https://ieeexplore.ieee.org/abstract/document/8987286
Published in arXiv preprint arXiv:1906.09587, 2019
Recommended citation: Amit Jaiswal, Ivan Panshin, Dimitrij Shulkin, Nagender Aneja, Samuel Abramov "Semi-supervised learning for cancer detection of lymph node metastases." arXiv preprint arXiv:1906.09587, 2019. https://arxiv.org/pdf/1906.09587.pdf
Published in 2020 2nd Symposium on Signal Processing Systems, 2020
(Conference Publication)
Recommended citation: Sandhya Aneja, Siti Nur, Nagender Aneja "Neural Machine Translation model for University Email Application." 2020 2nd Symposium on Signal Processing Systems, 2020. pp. 74--79 doi: 10.1145/3421515.3421522 https://dl.acm.org/doi/10.1145/3421515.3421522
Published in Proceedings of the 2020 the 4th International Conference on Big Data and Internet of Things, 2020
(Conference Publication)
Recommended citation: Rajarshi Chowdhury, Sandhya Aneja, Nagender Aneja, Emeroylariffion Abas "Network traffic analysis based iot device identification." Proceedings of the 2020 the 4th International Conference on Big Data and Internet of Things, 2020. pp. 79--89 doi: 10.1145/3421537.3421545 https://dl.acm.org/doi/10.1145/3421537.3421545
Published in Wireless Personal Communications, 2021
(Journal Publication)
Recommended citation: Nagender Aneja, Sapna Gambhir "Recent Advances in Ad-Hoc Social Networking: Key Techniques and Future Research Directions." Wireless Personal Communications, 2021. vol. 117 pp. 1735--1753 doi: 10.1007/s11277-020-07942-7 https://link.springer.com/article/10.1007/s11277-020-07942-7
Published in Data in Brief, 2021
(Journal Publication)
Recommended citation: Rajarshi Chowdhury, Sandhya Aneja, Nagender Aneja, Pg Abas "Packet-level and IEEE 802.11 MAC frame-level network traffic traces data of the D-Link IoT devices." Data in Brief, 2021. vol. 37 pp. 107208 doi: 10.1016/j.dib.2021.107208 https://www.sciencedirect.com/science/article/pii/S2352340921004923
Published in 2022 14th International Conference on COMmunication Systems & NETworkS (COMSNETS), 2022
(Conference Publication)
Recommended citation: Sandhya Aneja, Melanie En, Nagender Aneja "Collaborative adversary nodes learning on the logs of IoT devices in an IoT network." 2022 14th International Conference on COMmunication Systems & NETworkS (COMSNETS), 2022. pp. 231--235 doi: 10.1109/COMSNETS53615.2022.9668602 https://ieeexplore.ieee.org/document/9668602
Published in International Journal of Communication Networks and Distributed Systems, 2022
(Journal Publication)
Recommended citation: Sandhya Aneja, Nagender Aneja, Bharat Bhargava, Rajarshi Chowdhury "Device fingerprinting using deep convolutional neural networks." International Journal of Communication Networks and Distributed Systems, 2022. vol. 28 pp. 171--198 doi: 10.1504/IJCNDS.2022.121197 https://www.inderscienceonline.com/doi/10.1504/IJCNDS.2022.121197
Published in IAES International Journal of Artificial Intelligence (IJ-AI), 2022
(Journal Publication)
Recommended citation: Sandhya Aneja, Nagender Aneja, Pg Abas, Abdul Naim "Transfer learning for cancer diagnosis in histopathological images." IAES International Journal of Artificial Intelligence (IJ-AI), 2022. vol. 11( 1) doi: 10.11591/ijai.v11.i1.pp129-136 https://ijai.iaescore.com/index.php/IJAI/article/view/21133
Published in IAES International Journal of Artificial Intelligence (IJ-AI), 2022
(Journal Publication)
Recommended citation: Sandhya Aneja, Nagender Aneja, Pg Abas, Abdul Naim "Defense against adversarial attacks on deep convolutional neural networks through nonlocal denoising." IAES International Journal of Artificial Intelligence (IJ-AI), 2022. vol. 11( 3) doi: 10.11591/ijai.v11.i3.pp961-968 https://ijai.iaescore.com/index.php/IJAI/article/view/21503
Published in IAES International Journal of Artificial Intelligence (IJ-AI), 2022
(Journal Publication)
Recommended citation: Sandhya Aneja, Nagender Aneja, Ponnurangam Kumaraguru "Predictive Linguistic Cues for Fake News: A Societal AI Problem." IAES International Journal of Artificial Intelligence (IJ-AI), 2022. vol. 11( 4) doi: 10.11591/ijai.v11.i4.pp1252-1260 https://ijai.iaescore.com/index.php/IJAI/article/view/21798
Published in Wireless Communications and Mobile Computing, 2023
(Journal Publication)
Recommended citation: Nagender Aneja, Sandhya Aneja, Bharat Bhargava "AI Enabled Learning Architecture Using Network Traffic Traces over IoT Network." Wireless Communications and Mobile Computing, 2023. vol. 2023 doi: 10.1155/2023/8658278 https://www.hindawi.com/journals/wcmc/2023/8658278/
Published in International Journal of Intelligent Networks, 2023
(Journal Publication)
Recommended citation: Wang Hui, Nagender Aneja, Sandhya Aneja, Abdul Naim "Conversational chat system using attention mechanism for COVID-19 inquiries." International Journal of Intelligent Networks, 2023. doi: 10.1016/j.ijin.2023.05.003 https://www.sciencedirect.com/science/article/pii/S266660302300012X
Published in 10th Annual Conf. on Computational Science & Computational Intelligence (CSCI'23), 2023
(Conference Publication)
Recommended citation: Shafkat Islam, Nagender Aneja, Ruy Oliveira, Sandhya Aneja, Bharat Bhargava, Jason Hamlet, Chris Jenkins "Detect & Adapt: A Resiliency Enhancement Mechanism for Space Computing Platforms." 10th Annual Conf. on Computational Science & Computational Intelligence (CSCI'23), 2023. https://american-cse.org/csci2023-ieee/pdfs/CSCI2023-47UoKEqjHou6fHnm3C9aVb/615100a907/615100a907.pdf
Published in I Can’t Believe It’s Not Better (ICBINB): Failure Modes in the Age of Foundation Models, NeurIPS 2023, 2023
(Conference Workshop Poster Publication)
Recommended citation: Lixiang Li, Bharat Bhargava, Alina Nesen, Nagender Aneja "SentimentPulse: Temporal-Aware Custom Language Models vs. GPT-3.5 for Consumer Sentiment." I Can’t Believe It’s Not Better (ICBINB): Failure Modes in the Age of Foundation Models, NeurIPS 2023, 2023. https://nips.cc/virtual/2023/76523
Published:
This is a list of FYP/Research students.
Published:
This post covers projects available for FYP/Research students. Students may also contact with their project proposals.
Published:
This is a collection of some deep learning projects/papers.
Published:
The webinar was conducted by IEEE Collaborate Group on the white paper related to protecting Internet Traffic.
Published:
The talk covered topics related to a talk on Prior Art Search, Patentability Criteria, and introduction to Patent Drafting.
Published:
A webinar on introduction to deep learning and practical implementation of neural network and convolutional neural network in MNIST dataset.
Published:
Keynote Speech at International Conference (Virtual) Recent Trends in Computing (ICRTC-2021), Compucom Institute of Information Technology & Management, Jaipur, India
Published:
This talk is for IEEE Delhi.
Published:
Half-day workshop on Advanced Excel 365 on Advanced Excel Features.
Published:
Bachelor of Science (Computer Science), Universiti Brunei Darussalam, Digital Science, 2021
Students will learn the latest technologies including Python in the field of Internet Programming.
Bachelor/Master's Degree, Universiti Brunei Darussalam, 2021
Students will learn the Introduction to Patents and Patents Search.
Bachelor of Digital Science, Universiti Brunei Darussalam, Digital Science, 2022
Students will learn the latest technologies including Tableau in the field of data analytics.
For All, , 2023
Students will learn to write prompts for ChatGPT.
Short Term Course for visiting students of Singapore Management University, School of Digital Science, Universiti Brunei Darussalam., 2023
In this short-term course, students will learn to use digital technologies to create new or modify existing businesses.
Bachelor of Digital Science, School of Digital Science, Universiti Brunei Darussalam., 2023
Students will learn to use digital technologies to create new or modify existing businesses.
Bachelor of Digital Science, Universiti Brunei Darussalam, Digital Science, 2024
Students will learn the latest technologies, including Tableau, Python, and R.
Bachelor of Digital Science, School of Digital Science, Universiti Brunei Darussalam, 2024
Students will learn to apply deep learning techniques for projects from different industries.
B.S. Computer Engineering and B.S. Electrical Engineering, SEITZ 300, 2024
An introduction to applied software design methods for writing efficient, reusable, and modular C++ programs. Pre: 2574 with a C- or better. (3H, 3C)